- 2024-07-29: Messenger Comparison Updates (tbc..)
- 2024-06-25: New Smoke Release 2024.06.25
- 2023-08-04: McEliece Article
- 2018-01-05: Smoke Chat (Java) compatibility to Spot-On (C++) (FuriousFire Release)
- 2017-07-07: Smoke & SmokeStack as a private public key repository (key server) (Locke Release).
- 2017-07-04 (Independence Day): First Release of Smoke - Android Client with SmokeStack (Chat Server) (Jujube Release).
Download Client & Server
Please Download the Android-APK installers at this mirror here, at the Github-Development-Page or at F-Droid.
You need to set up an own so called Echo-Server via SmokeStack (Android Echo Server);
[or alternatively use a Echo-Listener via Spot-On (Desktop) or via Spot-On-Lite (Debian Headless).
For a Windows Echo-Server use Win32-Version Version 2023.01.15 (also probably update Win32 vcredist_x86.exe & Win64 vcredist_x64.exe on your webserver). Read more about Echo-Servers in the Reddit-Forum].
What is Smoke Messenger?
Smoke is an encrypting, open source, chat messenger application for mobile Android devices, like tablets and cell phones, written in Java.
Smoke is not like other alternatives*) ...
*) e.g. like Whatsapp, Telegram, Threema (to mention three most popular closed source applications) or Signal, GoldBug, Wire, Conversations, Chatsecure or Antox (to mention six alternatively relevant mobile crypto chat applications, which are open source - but do not allow to have an own chat server or do not meet other criteria mentioned below).
...as Smoke has these unique feature propositions in its basket:
-
with Smoke, you can easily run your own, decentralized and federatable private chat server (even mobile server for Android: SmokeStack Server or Spot-On Server for different Operation systems with bigger scale),
-
that also means that the application Smoke does not upload, copy and index (or some say steal) your phone book contacts. Instead shaere your key over an Alias or the Smoke-ID: a 32-digit SipHashID as Chat-ID is used, which looks like @1234-AEF2-EIA3-31DE-6789-GEF3-KIA6-55US and, more easily, any Alias can be defined by the user, to create a symmetric encrypted channel to transfer the keys.
-
option to manually specify individual encryption values, e.g. for size of key generation or own password-definition of end-to-end-encryption. The standard of Cryptographic Calling with Instant Perfect Forward Secrecy (IPFS) has been implemented into Smoke: Renew your end-to-end encryption whenever you want - instantly with one click on the "Call" button,
- Smoke is a mobile application for phones or tablets (witten in Java and currently compiled for Android, but should also compile for other devices - and, also there is a Qt C++ version, via the aplication Spot-On),
-
Open Source (BSD License) for both, mobile client and chat server.
- Smoke Messenger is know as the first quantum-computing secure McEliece-Messenger.
- The Grupchat is encrypted both: either symmetric (Fire Tab) or asymmetric (Chat Tab) Encryption. No other messenger has quasi GPG like Groupchat based on asymmetric encryption, in case all users in a group have shared keys.
Smoke is the only mobile crypto chat, which is open source, allows you to use your own decentral chat server, does not send your phone number to central servers or friends, and fifth, is able to define your own end-to-end enctypting passwords manually by your individual choice.
Smoke is known as the one of the first mobile Messenger, which implemented the quantum-computing secure McEliece algorihtm worldwide. Please read also here about McEliece-Messaging.
So far no other application matches these seven criteria.
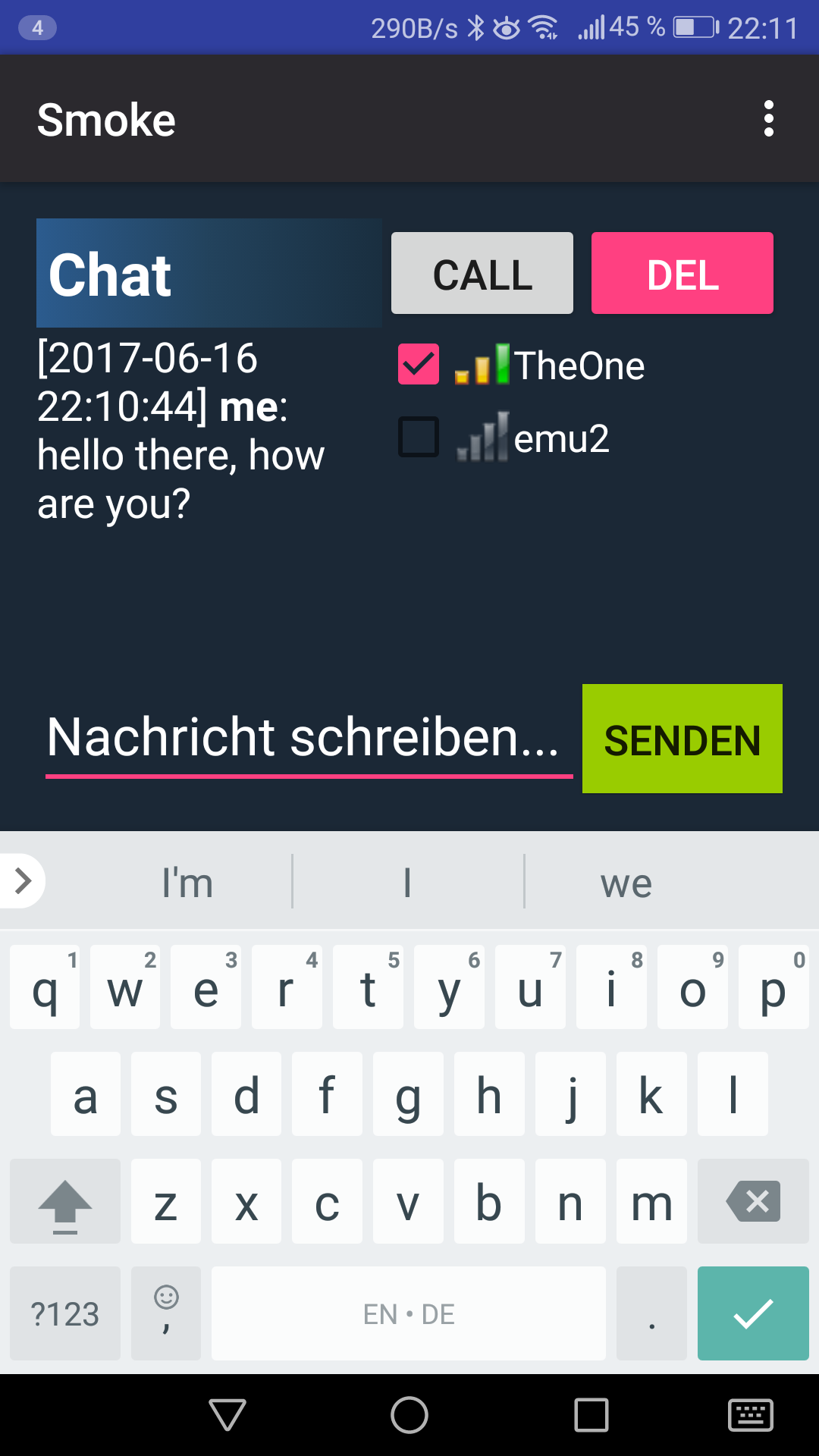
The screenshot shows the chat tab with dialogues to one or several marked friends. When the send button is green, you are connected to a server. If your friend shows a green Wifi-Symbol, she or he is online. Please press the Call button first to provide an AES-encryption layer. Layer means you change the (by default) asymmetric group chat to a symmetric group chat (via AES) per user.
Mobile Messenger Score Card
The following applications are currently comparable, please consider to choose only open source chat applications, which also have an open source chat server and provide you the option to enter individually and manually defined end-to-end encryption password-strings at any time:
Score Card for Mobile Cryptographic Chat Applications |
| ====CRITERIA==== |
Smoke |
Whatsapp |
SpotOn |
Telegram |
Threema |
GoldBug |
Signal |
Wire |
|
Briar |
Chat secure |
Element |
Q/AnTox |
|
SimpleX |
Session |
Riochet2 |
Quiet |
Cwtch |
Berty |
Meshenger |
Keychat |
Status |
Mobile App |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Client Open Source |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Encrypted communications. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Quantum Immun: McEliece (Fujisaka or Pointcheval or Super-McEliece: m=13/t=118) or NTRU or CRYSTALS-Kyber |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Own Open Chat Server |
|
|
|
|
|
|
|
BETA |
|
|
|
|
|
IMAP |
|
|
Mobile Server available (APK) |
|
 |
 |
 |
 |
 |
 |
 |
 |
DHT |
 |
 |
DHT |
./. |
DHT |
DHT |
No Phone Number required = No Number Upload: Use of Aliases. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Text in HDD-SQL encrypted |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
#BYOK: Bring Own E2E-Key/#CSEK |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Attachments saved encrypted |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Multiple devices |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Man. renew sess key ("Crypto-Calling")  
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Obfuscation of secret keys in RAM
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Chat to offline friends: Post offices for messages of the past (e.g. by Ozone dest.) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Groupchat |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Sym Encr. Groupchat |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Asym Encr. Groupchat |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Payment free |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
´
Argon2id and/or PBKDF2 hash |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Rainbow digital signature scheme |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
SPHINCS digital signature scheme |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Automatic public-key exchange (AutoCrypt) |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
No Metadata |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Serverless P2P Capability / Decentralized by TCP & UDP multicast/unicast |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
End-to-End-Encryption |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
File-Sharing |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Completly decentralized & federatable |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Application lock |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Saving in locked containers: Content is recorded & saved via authenticated encryption |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Juggling Juggernaut Protocol  |
|
>
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Library Free: Almost zero-dependency software. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
F-Droid: Alternative Store |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
17 |
5 |
15 |
5 |
4 |
15 |
6 |
8 |
9 |
9 |
9 |
7 |
6 |
10 |
10 |
8 |
Source: https://smokeappope.sourceforge.io/ | Status: 07/2024 |
-
 Juggling Juggernaut Protocol: The 'Juggling Juggernaut Protocol' is part of the cryptographic mechanisms in the Smoke Messenger project, which is an open-source initiative designed to provide secure and encrypted communications. The protocol is involved in managing secure communications within the Smoke system, particularly by handling the exchange and management of public keys in a way that is robust and resistant to certain types of cryptographic attacks. The protocol likely implements some form of key juggling, which involves dynamically adjusting and managing keys during the communication process to enhance security. This can help protect against attempts to intercept or tamper with the data being exchanged. The Juggling Juggernaut Protocol is part of a broader suite of security features in Smoke, including the use of advanced cryptographic algorithms and protocols like McEliece and Rainbow digital signatures, which are designed to ensure that communications are not only encrypted but also resistant to quantum computing threats.
Juggling Juggernaut Protocol: The 'Juggling Juggernaut Protocol' is part of the cryptographic mechanisms in the Smoke Messenger project, which is an open-source initiative designed to provide secure and encrypted communications. The protocol is involved in managing secure communications within the Smoke system, particularly by handling the exchange and management of public keys in a way that is robust and resistant to certain types of cryptographic attacks. The protocol likely implements some form of key juggling, which involves dynamically adjusting and managing keys during the communication process to enhance security. This can help protect against attempts to intercept or tamper with the data being exchanged. The Juggling Juggernaut Protocol is part of a broader suite of security features in Smoke, including the use of advanced cryptographic algorithms and protocols like McEliece and Rainbow digital signatures, which are designed to ensure that communications are not only encrypted but also resistant to quantum computing threats.
-

 Cryptographic Calling (e.g. manually re-new session keys): Cryptographic Calling is a way to provide end-to-end credentials over a secure connection. The temporary key can be a-symmetric (PKI) or symmetric (a password string also known as a passphrase). The idea is to make end-to-end encryption as easy as calling a partner over a phone, just taking the phone, call, and if the session has to end, to change the temporary keys again and quit the call. Hence, a “Call” transfers over a public/private key encrypted environment a symmetric key (e.g. AES). It is a password for the session talk, only the two participants know. With one click the user can instantly renew the end-to-end encryption password for the talk, respective text chat. It is also possible to manually define the end-to-end encrypted password (manually defined Calling). There are several further different ways to call: There are several further different ways to call: Asymmetric Calling, Forward Secrecy Calling, Symmetric Calling, SMP-Calling and 2-Way-Calling. The term of a “Call” in Cryptography, respective 'Cryptographic Calling' has been introduced by the Spot-On Encryption Application and refers to sending a new end-to-end encryption password to the other participant over an already secure stablished channel. See also the Figure: Overview of the different types of Cryptographic Calling with respective criteria: https://www.reddit.com/r/Spot_On_Encryption/comments/1de0ajn/spoton_encryption_suite_faq_figure_overview_of/
Cryptographic Calling (e.g. manually re-new session keys): Cryptographic Calling is a way to provide end-to-end credentials over a secure connection. The temporary key can be a-symmetric (PKI) or symmetric (a password string also known as a passphrase). The idea is to make end-to-end encryption as easy as calling a partner over a phone, just taking the phone, call, and if the session has to end, to change the temporary keys again and quit the call. Hence, a “Call” transfers over a public/private key encrypted environment a symmetric key (e.g. AES). It is a password for the session talk, only the two participants know. With one click the user can instantly renew the end-to-end encryption password for the talk, respective text chat. It is also possible to manually define the end-to-end encrypted password (manually defined Calling). There are several further different ways to call: There are several further different ways to call: Asymmetric Calling, Forward Secrecy Calling, Symmetric Calling, SMP-Calling and 2-Way-Calling. The term of a “Call” in Cryptography, respective 'Cryptographic Calling' has been introduced by the Spot-On Encryption Application and refers to sending a new end-to-end encryption password to the other participant over an already secure stablished channel. See also the Figure: Overview of the different types of Cryptographic Calling with respective criteria: https://www.reddit.com/r/Spot_On_Encryption/comments/1de0ajn/spoton_encryption_suite_faq_figure_overview_of/
-


 Fiasco Forwarding Secrecy: 'Fiasco Forwarding Secrecy' is a concept related to cryptographic security within the Smoke project, an open-source communication framework focused on providing secure, encrypted messaging and data exchange. This feature, as the name suggests, likely ties into forward secrecy (also known as perfect forward secrecy), a principle in cryptography that ensures that even if a private key is compromised, previous communication sessions cannot be decrypted retroactively. Fiasco Forwarding (FF) is carried out by Fiasco Keys as temporary keys, which were first introduced in the application of the Smoke Crypto Chat messenger, which is semi compatble with the Spot-On Encryption Suite application. These keys consist of a handful of temporary keys for end-to-end encryption. Instead of one key per session (see OTR) or one key per message (cf. OMEMO or Double Ratchet, Signal protocol), several keys per message are sent, only one of which is valid. This is a more volatile design that significantly increases security. Fiasco Forwarding is therefore a successor architecture of protocols with just one key per session or message. In the Smoke Messenger documentation is is referred to Fiasco Keys and Fiasco Forwarding: Authentication and encryption key data which are established via the so-called 'Cryptographic Calling' mechanism are recorded within the participants-keys database table. Whenever a message from a SmokeStack- or Spot-On-Server-instance is received, the message’s digest is verified using each of the recorded authentication keys. This Messenger iterates through the set of Fiasco authentication keys until a correct authentication key is discovered or the search is exhausted. If an authentication key is recovered, the message is deciphered and delivered locally. Newer authentication keys are tested first. A key pair has a lifetime of 864,000 seconds. Spot-On implemented a similar process by Secret Stream Keys. See the technical documentation for details, differences and technical implementations. Fiasco Forwarding is a follow-up state-of-the-art paradigm next to 'one key per session* and/or 'one key per message': Sending a bunch of dozen keys. In the context of Smoke, FF Secrecy likely refers to an innovative implementation of forward secrecy within their communication protocols. It might involve advanced techniques to ensure that session keys are ephemeral, meaning they are generated for each session and not reused. This enhances security by ensuring that each session's keys are isolated and independent, so that the compromise of one key doesn't affect the security of past or future communications. Given the focus on secure and resilient cryptographic systems in Smoke, FF Secrecy plays a crucial role in maintaining the confidentiality and integrity of communications against a wide range of attacks, including those that might arise from future advances in computing, such as quantum computing. The name 'Fiasco' may be coining a particular advanced protocol respective approach within the Smoke project's suite of cryptographic tools.
Fiasco Forwarding Secrecy: 'Fiasco Forwarding Secrecy' is a concept related to cryptographic security within the Smoke project, an open-source communication framework focused on providing secure, encrypted messaging and data exchange. This feature, as the name suggests, likely ties into forward secrecy (also known as perfect forward secrecy), a principle in cryptography that ensures that even if a private key is compromised, previous communication sessions cannot be decrypted retroactively. Fiasco Forwarding (FF) is carried out by Fiasco Keys as temporary keys, which were first introduced in the application of the Smoke Crypto Chat messenger, which is semi compatble with the Spot-On Encryption Suite application. These keys consist of a handful of temporary keys for end-to-end encryption. Instead of one key per session (see OTR) or one key per message (cf. OMEMO or Double Ratchet, Signal protocol), several keys per message are sent, only one of which is valid. This is a more volatile design that significantly increases security. Fiasco Forwarding is therefore a successor architecture of protocols with just one key per session or message. In the Smoke Messenger documentation is is referred to Fiasco Keys and Fiasco Forwarding: Authentication and encryption key data which are established via the so-called 'Cryptographic Calling' mechanism are recorded within the participants-keys database table. Whenever a message from a SmokeStack- or Spot-On-Server-instance is received, the message’s digest is verified using each of the recorded authentication keys. This Messenger iterates through the set of Fiasco authentication keys until a correct authentication key is discovered or the search is exhausted. If an authentication key is recovered, the message is deciphered and delivered locally. Newer authentication keys are tested first. A key pair has a lifetime of 864,000 seconds. Spot-On implemented a similar process by Secret Stream Keys. See the technical documentation for details, differences and technical implementations. Fiasco Forwarding is a follow-up state-of-the-art paradigm next to 'one key per session* and/or 'one key per message': Sending a bunch of dozen keys. In the context of Smoke, FF Secrecy likely refers to an innovative implementation of forward secrecy within their communication protocols. It might involve advanced techniques to ensure that session keys are ephemeral, meaning they are generated for each session and not reused. This enhances security by ensuring that each session's keys are isolated and independent, so that the compromise of one key doesn't affect the security of past or future communications. Given the focus on secure and resilient cryptographic systems in Smoke, FF Secrecy plays a crucial role in maintaining the confidentiality and integrity of communications against a wide range of attacks, including those that might arise from future advances in computing, such as quantum computing. The name 'Fiasco' may be coining a particular advanced protocol respective approach within the Smoke project's suite of cryptographic tools.
- Please note, that Wire Server Software is currently only scheduled for an open source code release and not yet any Third Party Community Server has been announced to be online. At the moment it contains only a subset of the libraries and services and the release process is not yet fully done.
- Please note, that the Signal Server Software is dependent on SMS-Verification Services and Amazon Web Services and cannot be rebuild without a focus on the complex ecosystem, means: No one yet has set up an alternative Signal-Server for the offered client. That's why the indication has been set to not open source, respective "own open chat server" is possible. It is not guaranteed, that the released source of the server is as the current server running and if there are additional plugins running compromising the security.
- Please note, that Chatsecure and Conversatons need to support for multiple devices special server software and requirements (e.g. prosody & ejabberd servers with XEP 0280 and XEP 0313). Only a few server software installers out of 24 xmpp server projects are functional for the extended crypto of these applications *).
- Please note, that Chat to offline friends in Smoke is provided over the Ozone feature like a post box.
- Please note, that GoldBug Crypto Chat is mobile available only for MS Windows on tablets and phones, and offline chat is provided over the POPTASTIC feature (p. 134*)), which requires an IMAP or POP3 account.
- Please note, that the Telegram application source code is indeed released to public, but hardly will "not allow to develop a different client as the open source code isn’t "reusable*).
- Please note, that Conversations is not payment free on play store.
- Please note, that Briar can only add friends, you have met in person.
- Please note, that this "mobile" score card uses only fundamental technologic and architectural approaches as criteria.
However, in the long run mobile crypto chat applications with decentral open source chat servers will be fundamental, which are easy to set up and administer. Smoke enables an open source chat server handling encrypted chat within every school, community and family as an option. Smokestack Server Software provides that even as a mobile server on Android.
What does Smoke mean for you?
Smoke might have several connotations for every user - what is yours?
-
Smoke is a Sign or Signal for communication over distances?
-
Smoke creates an alternative to the clouds?
-
Smoke-A-Pope? No! There is no religious context mentioned or intended.
-
SmokeApp OPE ? Yes - Online Poem Encryption with SmokeApp OPE @sourceforge.io.
-
Make a pause at work to smoke?
-
Meet friends, while you smoke?
-
Smoke is your feedom to commuicate secure?
-
Smoke shows that crypto analysts are on fire?
- Using smoke does not generate cancer.
-
Using Smoke is "back to the roots" in messaging friends?
- Show white smoke when successful? Perhaps.
Smoke is not driven by any commercial party. Developers are welcomed e.g. to fork and improve the Graphical User Interface (GUI), as the licensce is open BSD and the code may be used by everyone.
The screenshot shows the chat window with those friends checked, who should receive your message. The "Call" button creates a new end-to-end encryption (via AES) instantly ("Cryptographic Calling"). Online Friends have a status icon, friends without keys are also highlighted and need to go through the SipHashID exchange and "Share Keys" button action (via the Echo-Public-Key-Share-(EPKS)-Protocol).
Don't worry, it's easy: just exchange your SIpHashID or Alias with your friend, and press the green "Share Keys" button. Over this generated channel your asymmetric RSA keys are exchanged and the encrypted conversation can start after a Call: The "Cryptographic Calling" (see "Call"-button in the chat tab) provides a symmetric encryption (AES) to create "Forward Secrecy" in your end-to-end encryption with session keys.

The screenshot shows how easy it is to add a Neighbor/Server IP-Address.
Encryption within Smoke: Multi-Encryption
The encryption within Smole utilizes a hybrid multiencryption, that means asymmetric (public keys, RSA) and symmetric keys (AES) are used. Your message is encrypted multiple times.
Once the set up is done, the public key of your asymmetric encryption (RSA) is turned into a session based symmetric encryption (AES).
You can instantly renew the end to end enctyption, Forward Secrecy is known as Instant Perfect Forward Secrecy (IPFS). Also you can use your own end to end encryption key (Customer Supplied Encryption Key, #CSEK).
Alias or SipHashID Exchange & Share Keys: No Phone number upload
Many applications upload and expose your complete phone book and friends list. Also you need to provide a new friend your phone number to be able to chat to you. Smoke is different. With Smoke you need not to give your phone number away nor you need to upload all your friends contact details to a central server, which might even cause a legal problem in several countries. Smoke uses a dedicated "SipHashID" as a Chat-ID. Just share with your friend your SipHashID, which has a 16 digit format like: @1234-DE3A-32BC-E78A.
When both have exchanged and entered the SipHashID of the friend, just press the green "Share Keys" button and your encryption keys are transferred to each other (via the Echo-Public-Key-Sharing Protocol (EPKS)). A key icon shows the success of the transfer. An easy way to provide encryption keys with a short identifier. The Echo-Public-Key-Sharing-Protokoll over the "Share Keys" Button works best, if both friends use the same chat server.

Open Source License: You own this application!
Smoke is open source, also the server software is open soure. The license is a simple BSD license, that means everyone can grab and use the code. Only the BSD license has to be kept. In this regard the code is available for everyone and everyone might use it. Smoke is an elaborated encryption application that is available for the public. Because of the open source mentality the code can be inspected and compiled by everyone. Backdoors are not possible and for this reason never choose or trust a closed source crypto application.
Federatable, Decentral Chat Servers: Create your own!
Smoke does not rely on one central chat server. Everyone can set up an own decentral crypto chat server for the own group, school or family. The chat servers can be connected amoung each others to a federation (network). It is a concept like decentral chat servers of XMPP, but has e.g. the advantage, that to set up an own server is much more easy - and even mobile Android servers are possible. Smoke uses the HTTPS protocol for a chat server, which is going through any firewall, the setup of a server is a two click install and does not require any special admin knowledge. HTTPS-chat-servers are the successor of XML-chat-servers over complicated protocols or difficult server install-routines. The server software for Smoke can be found at spot-on.sf.net. Also there is SmokeStack - a mobile server under Android for Smoke (see below). The Smoke application provides a test and development server-IP address under: dolphin-ipv4.cloud.tilaa.com and TCP-port 4710. Please use this server only for your scientific research and help to set up an own server for your friends.
End-to-End Encryption: Manual definition of e2e
Your encryption to your friends does not use permanent encryption keys, instead session-based ephemeral (temporary) keys are used. You can renew your end to end encryption at any time you want - using the "Call" Button for "Cryptographic Calling". And: You can use your own password-string for end to end encryption, which is individually and manually defined by yourself. As far as it is known no other application provides currently the option that you define manually a 32-digit AES like Password on your own in such a mobile encryption application. Just tap your finger a few seconds in the chat tab on a friend and get the context menu for a "custom" password entry provided.

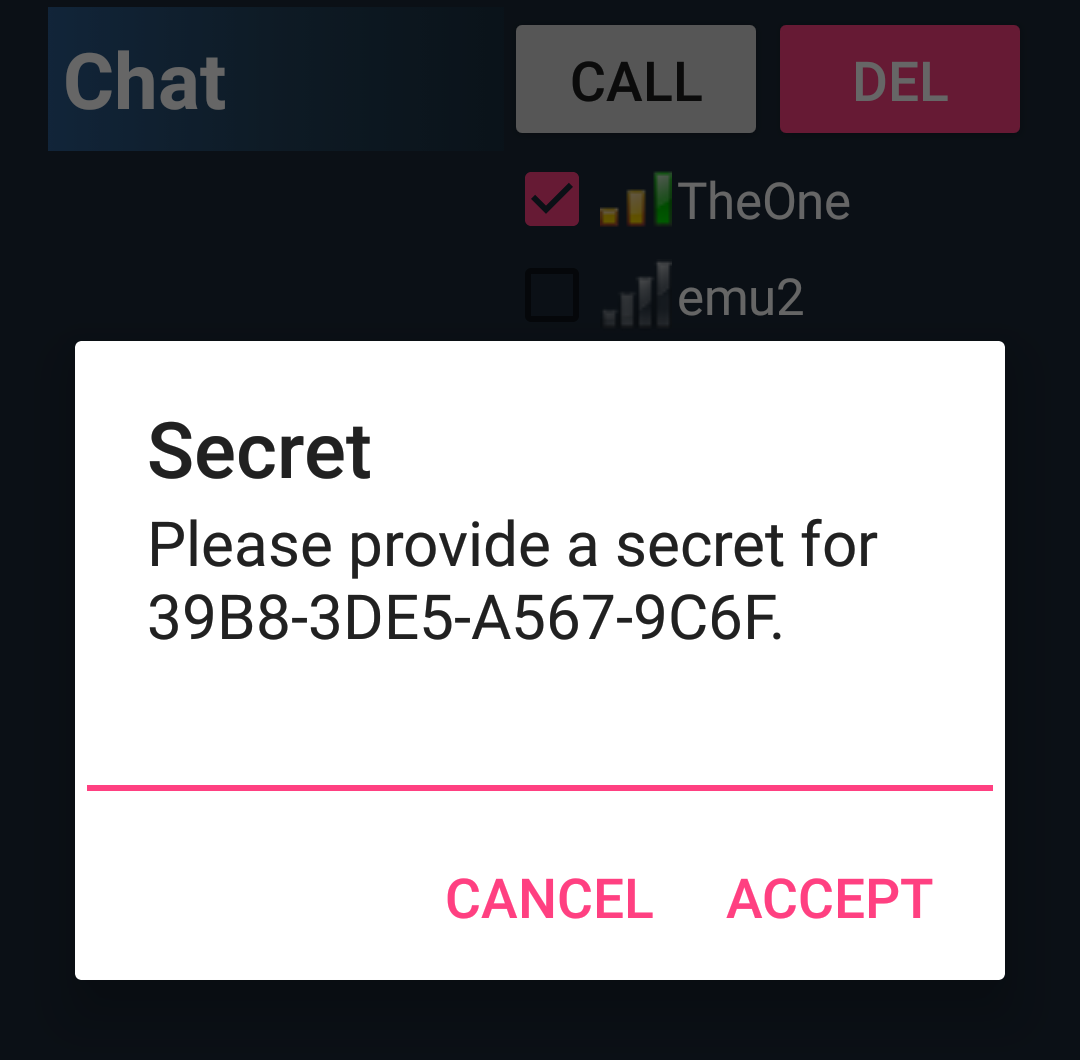
Use your own session keys: Individual and instant session keys
Under the hashtag #CSEK is discussed that users or customers supply own encryption keys (CSEK - Customer Supplied Encryption Key). With Smoke you can define individually at any time that you want to renew your session based key instantly. This is the concept of Instant Perfect Forward Secrecy and is done via the "Cryptographic Calling" function. Just press the "Call" button and instantly a new session key is provided. The new session key (AES-String) is generated 50% by you and answerd with 50% of the key by your friend. This makes your conversation deniable.
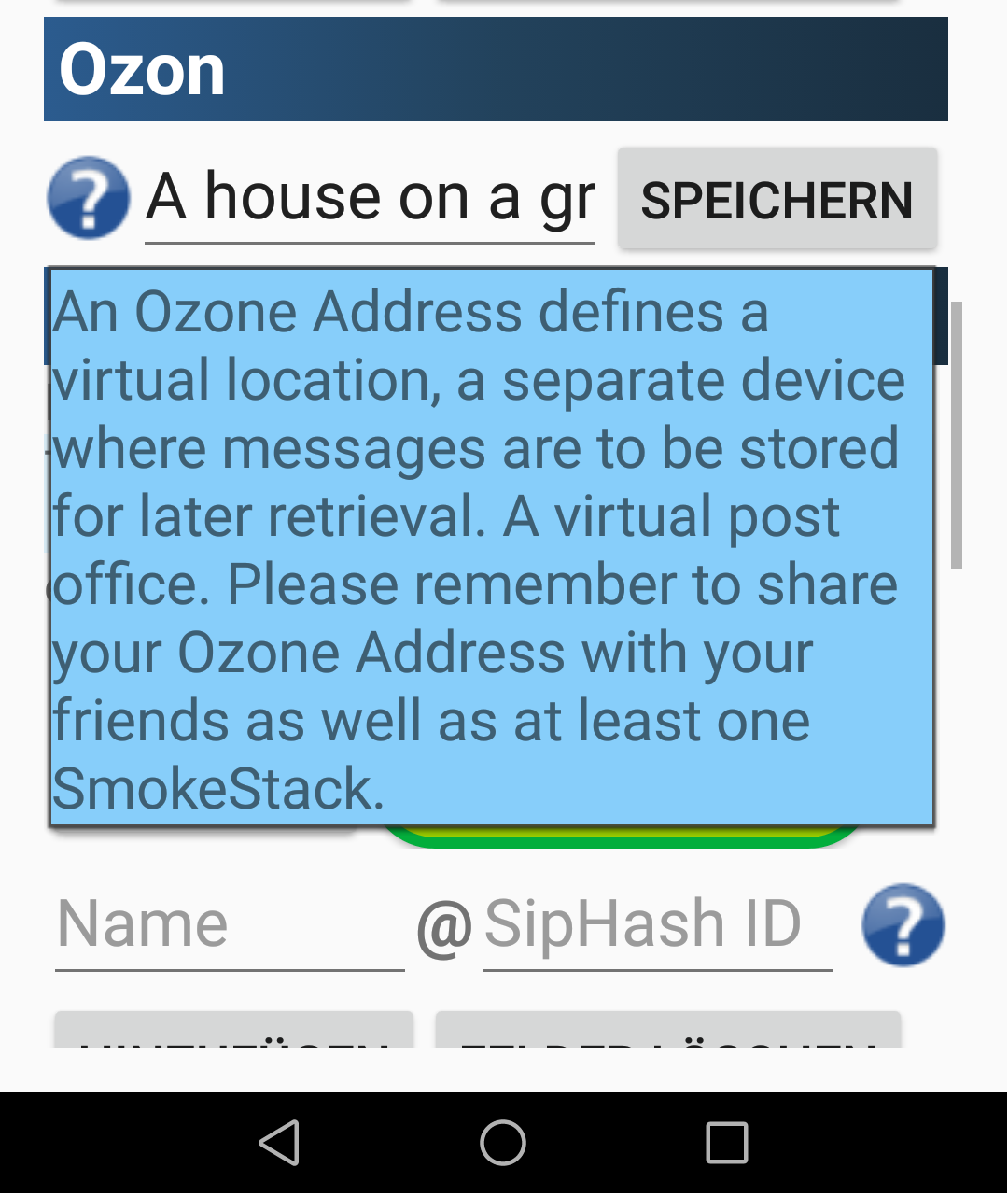
Ozone - How to add Ozone to Smoke
Ozone is a function in Smoke, to define a password. If this password with your SipHashID is stored in the server "SmokeStack" and also by your friends - you have a common virtual address which lets you retrieve messages like from a postbox, in the case you have been offline with your mobile device. That means: An Ozone Address defines a virtual location, a separate device where messages are to be stored for later retrieval. A virtual post office box. Please remember to share your Ozone Address with your friends as well as at least one SmokeStack.
SmokeStack - An open mobile encrypting chat server
As a chat server, which can handle your encrypted packets, you can use either a Spot-On Server (c++) or - on a mobile (Android) device now: SmokeStack. Smoke App with SmokeStack (Server) seems to be one of the worldwide first projects with an open source mobile encrypting chat server. An own decentral and easy to set up chat server for every family and every school!
With the latest release SmokeStack is also a Key-Server: Even if you are offline, and your firend enters your the SIpHash Chat ID, Smokestack returns your public encryption key. This method reduces the fake entries of many searchable PGP-Email-Servers, as only your verified client submitts the credentials to a SmokeStack Key server.
Smokestack is open source (Java) and a mobile chat server for Android. You can set it easily up on your mobile phone, your tablet or an Android Box-PC for your TV-station, which are cheap to buy and constantly powered (e.g. octa-core boxes with S912 processors).
Bring your own crypto server on Android in your pocket! #BYOCS.
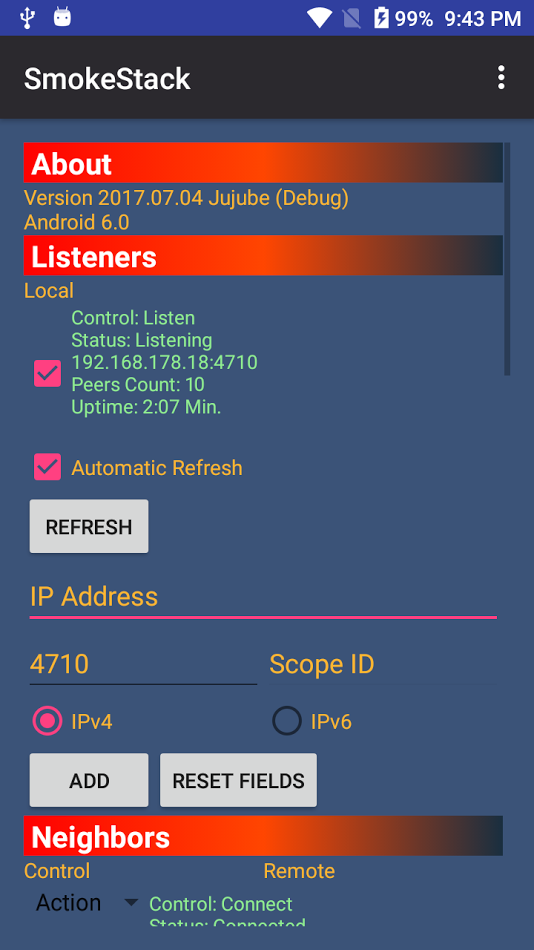
Multiple Device Support
Smoke allows to support multiple devices at the same time. Just copy your key to another device and you also receive the messages there. Have you experienced that Whatsapp in the Browser is defunctional, if your mobile device is not connected to the internet? Or that your XMPP app works only on several servers, if your server admin does not use a special software extension with dedicated modules? Smokestack server is easy to set up on Android and provides you messages for any Android device you want to use.
Mobile Platform: e.g. Android
As said: Smoke is an application for mobile devices. Because it is written in Java, it addresses many operating systems, the compile and builds are currently provided and adjusted for Android starting with the Android 4.4. KitKat version and up. This covers over 90 % of the current market share devices of Android.
Filetransfer
Also File Transfer is possible, e.g. pictures in the 1:1 chat window or share files over the Steam Protocol in the Share Tab. Steam allows to swarm files transfered even among friends, who have not exchanged keys, and though the transfer is secure end-to-end encrypted between friends, who have shared a key. Explore this protocol, which creates seccurity for friends, who have exchanged keys and also peers, who are not sharing a key with a friend, but are also able to swarm the transfer, in case a friend have sent them the file. Furthermore the File can be sent over the Stream Protocol to SSH Clients, without having Smoke installed. That is interoperability with zero dependencies.
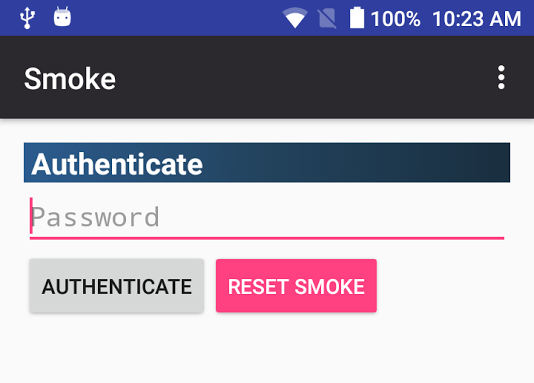
The screenshot shows how easy it is to log with your password into your SmokeApp.
Innovative Cryptographic Feature: Cryptographic Calling
Cryptographic Calling (e.g. manually re-new session keys): Cryptographic Calling is a way to provide end-to-end credentials over a secure connection. The temporary key can be a-symmetric (PKI) or symmetric (a password string also known as a passphrase). The idea is to make end-to-end encryption as easy as calling a partner over a phone, just taking the phone, call, and if the session has to end, to change the temporary keys again and quit the call. Hence, a “Call” transfers over a public/private key encrypted environment a symmetric key (e.g. AES). It is a password for the session talk, only the two participants know. With one click the user can instantly renew the end-to-end encryption password for the talk, respective text chat. It is also possible to manually define the end-to-end encrypted password (manually defined Calling). There are several further different ways to call: There are several further different ways to call: Asymmetric Calling, Forward Secrecy Calling, Symmetric Calling, SMP-Calling and 2-Way-Calling. The term of a “Call” in Cryptography, respective 'Cryptographic Calling' has been introduced by the Spot-On Encryption Application and refers to sending a new end-to-end encryption password to the other participant over an already secure stablished channel. See also the Figure: Overview of the different types of Cryptographic Calling with respective criteria: https://www.reddit.com/r/Spot_On_Encryption/comments/1de0ajn/spoton_encryption_suite_faq_figure_overview_of/
Innovative Cryptographic Feature: Fiasco Forwarding Secrecy
'Fiasco Forwarding Secrecy' is a concept related to cryptographic security within the Smoke project, an open-source communication framework focused on providing secure, encrypted messaging and data exchange. This feature, as the name suggests, likely ties into forward secrecy (also known as perfect forward secrecy), a principle in cryptography that ensures that even if a private key is compromised, previous communication sessions cannot be decrypted retroactively. Fiasco Forwarding (FF) is carried out by Fiasco Keys as temporary keys, which were first introduced in the application of the Smoke Crypto Chat messenger, which is semi compatble with the Spot-On Encryption Suite application. These keys consist of a handful of temporary keys for end-to-end encryption. Instead of one key per session (see OTR) or one key per message (cf. OMEMO or Double Ratchet, Signal protocol), several keys per message are sent, only one of which is valid. This is a more volatile design that significantly increases security. Fiasco Forwarding is therefore a successor architecture of protocols with just one key per session or message. In the Smoke Messenger documentation is is referred to Fiasco Keys and Fiasco Forwarding: Authentication and encryption key data which are established via the so-called 'Cryptographic Calling' mechanism are recorded within the participants-keys database table. Whenever a message from a SmokeStack- or Spot-On-Server-instance is received, the message’s digest is verified using each of the recorded authentication keys. This Messenger iterates through the set of Fiasco authentication keys until a correct authentication key is discovered or the search is exhausted. If an authentication key is recovered, the message is deciphered and delivered locally. Newer authentication keys are tested first. A key pair has a lifetime of 864,000 seconds. Spot-On implemented a similar process by Secret Stream Keys. See the technical documentation for details, differences and technical implementations. Fiasco Forwarding is a follow-up state-of-the-art paradigm next to 'one key per session* and/or 'one key per message': Sending a bunch of dozen keys. In the context of Smoke, FF Secrecy likely refers to an innovative implementation of forward secrecy within their communication protocols. It might involve advanced techniques to ensure that session keys are ephemeral, meaning they are generated for each session and not reused. This enhances security by ensuring that each session's keys are isolated and independent, so that the compromise of one key doesn't affect the security of past or future communications. Given the focus on secure and resilient cryptographic systems in Smoke, FF Secrecy plays a crucial role in maintaining the confidentiality and integrity of communications against a wide range of attacks, including those that might arise from future advances in computing, such as quantum computing. The name 'Fiasco' may be coining a particular advanced protocol respective approach within the Smoke project's suite of cryptographic tools?.
Innovative Cryptographic Feature: Juggling Juggernaut Protocol
Juggling Juggernaut Protocol: The 'Juggling Juggernaut Protocol' is part of the cryptographic mechanisms in the Smoke Messenger project, which is an open-source initiative designed to provide secure and encrypted communications. The protocol is involved in managing secure communications within the Smoke system, particularly by handling the exchange and management of public keys in a way that is robust and resistant to certain types of cryptographic attacks. The protocol likely implements some form of key juggling, which involves dynamically adjusting and managing keys during the communication process to enhance security. This can help protect against attempts to intercept or tamper with the data being exchanged. The Juggling Juggernaut Protocol is part of a broader suite of security features in Smoke, including the use of advanced cryptographic algorithms and protocols like McEliece and Rainbow digital signatures, which are designed to ensure that communications are not only encrypted but also resistant to quantum computing threats.
Innovative Cryptographic Feature: Steam Protocol / Steam Ephemeral Key Exchange
Steam Protocol: End-to-End encrypted file transfer with the Steam protocol with renewing credentials online. Please see details at the technical documentation or here.
How does Smoke work? - Short Manual Section of the Process Steps
Here are some of the salient points regarding the Smoke usage process:
- Install:
- Please download the APK Installer of Smoke from the provided repositories and install it on your device.
- In case you have not set the option in your Android settings to allow foreign installers from outside of the Google Playstore, please provide this option.
- Compiling:
- If you want to compile Smoke on your own, just download the source and load it in Android Studio. The Process is very easy and generates the APK Installer file.
- The Source can be found on Github at: github.com/textbrowser/smoke
- Key Generation:
- After installing the application Smoke requests you to provide a login password. If you want to keep it easy, choose 5 times a shorter password e.g. like "SmokeSmokeSmoke" or try just one letter "y".
- Server connection: Add a neighbor /= server:
- You need to connect to a chat server, which is done in the settings page/neighbor- server section. You can set up your own chat server using the software from spot-on.sf.net. Otherwise try the Smokestack server on android.
- Add Friend / Key Exchange:
- To add friend, please request and exchange the Alias or SipHashID
- Both friends need to enter the Alias or SipHashID of the other friend. If done, make sure, you are connected to a common chat server and then press the "Share Keys" button.
- The EPKS Protocoll for Echo Public Key Sharing transfers within your SipHashID-Channel your RSA-Keys (or McEliece Keys). If this has been successfully made, your friends shows up in the participants table with a key-icon. Otherwise your friend still has a warning symbol, which indicates, that the "Share-Keys"-Process has not been completed yet.
- If the friend has been added, next the the "Chat Tab" also a Tab "Windows Chat" will get visible for 1:1 chat. The Chat-Tab allows asymmetric group chat, the 1:1-Chat is a chat to just one friend.
- Chatting:
- Once both friends are shown in the friends list of the Chat Page (or also in the participants table in the settings page with a key-icon), the chat can start, just check the check-box of the friend you want to talk to, press the "Call" button and send a message.
- Cryptographic Calling: End-to-End encryption:
- In a chat session with your friend you might want to add another security layer by using a chat over symmetric AES encrytption. For that, just press the Call-Button and the Chat switches to a symmetric encryption to provide Instant Perfect Forward Secrecy (IPFS).
- Also you can enter manually an individually defined password like "smoke". Just tap a few seconds on a friend to call the context menu and choose "custom" to enter the password, both friends use.
- Ozone - virtual post box for offline messages:
- Define a password and enter it together with your SIpHashID into the SmokeStack-Server and create a virtual private post box in a third node to retrieve your messages - in case you have been offline. The Smokestack server will not be able to read your stored messages as they are encrypted with your public key.
Screenshots
Here are a few screenshots (Chat Window, Settings, Neighbor Table, Friendslist). Feel free to improve the GUI within your forked code contributions. More Screenshots will follow.
Download & Source
The Smoke decentralized chat application is an early functional release. If you'd like to help in improving/testing the network or graphical user interface, then please join with requests and offers over Github.